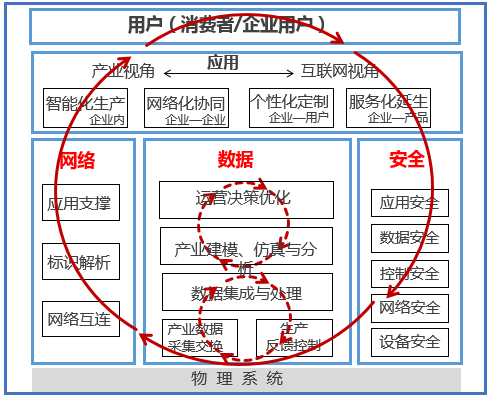
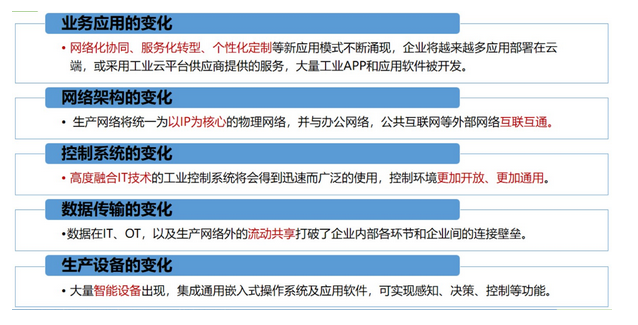
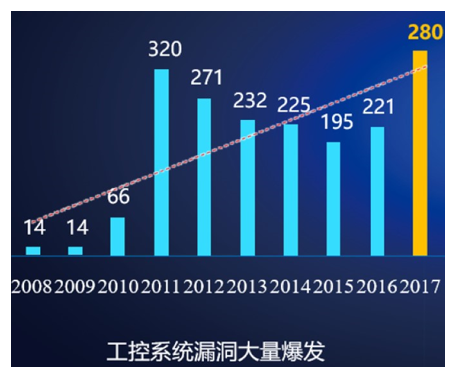
With the revolutionary breakthrough of Internet information technology and industrial automation technology and the development of global economic integration, the industrial Internet emerged at the historic moment and quickly became a hot technology, becoming a hot topic for continuous research and continuous exploration in the international industry. After recent years of development, the popularization of the Industrial Internet has provided more internal driving forces for the development of industrial economy. In order to better stimulate the technological potential of the Industrial Internet and lead the industrial Internet technology to realize the development of technical applications, the Industrial Internet Consortium (IIC) was established in 2014, dedicated to sharing the comprehensive use of the Internet to realize the reform and innovation of the intelligent application of machinery and equipment. my country also established the Industrial Internet Industry Alliance in 2016, demonstrating the determination and great prospects of my country's industrial Internet development. Industrial Internet is a key network infrastructure with low latency, high reliability, and wide coverage to meet the needs of industrial intelligent development. It is an emerging business and application model formed by the deep integration of a new generation of information and communication technology and advanced manufacturing. Among them, the network system is the basis for realizing the connection of the entire industrial system, the entire value chain, and the entire industrial chain, including the three major systems of network interconnection, identification analysis, and application support. The data includes "collection and exchange-integrated processing-modeling analysis-decision-making and control", forming an optimized closed loop and driving industrial intelligence. Security is the security guarantee for various fields and environments of the industrial/industrial Internet, including equipment security, control security, network security, application security, and data security. In order to accelerate the improvement of the application quality and effects of the Industrial Internet, contribute to my country’s economic restructuring and kinetic energy conversion, and comprehensively promote the "Made in China 2025" and "Internet +" action plans, it is necessary to focus on the national cyber security law and cyber security level protection The system strengthens the study of solutions in the field of industrial Internet information security for central enterprises. With the development of the Industrial Internet and the application of new technologies, the industrial network of central enterprises has undergone tremendous changes from multiple levels such as production equipment, control systems, network architecture, business applications, and data transmission. How to deal with security risks under the new changes has become a vital and urgent issue. Operating system vulnerabilities The technical framework of PC+Windows has now become the mainstream of the upper computer/operating station of the control system. In the control network, the upper computer/operating station is the main network node that realizes the communication with the MES, so the loopholes in its operating system have become a shortcoming in the information security of the entire control network. Operating system vulnerabilities frequently occur, and security incidents occur from time to time. Take the Windows XP version as an example, a large number of vulnerabilities have been discovered, such as input method vulnerabilities, IPC$ vulnerabilities, RPC vulnerabilities, Unicode vulnerabilities, IDA&IDQ buffer overflow vulnerabilities, Printer overflow vulnerabilities, Cookie vulnerabilities and so on. Most of these vulnerabilities are hugely harmful, and malicious code can gain complete control of the Windows XP operating station through these vulnerabilities, and even do whatever it wants. Industrial control system vulnerabilities Since the early industrial control systems all operated in a relatively independent network environment, only functionality and stability were considered during product design and network deployment, and security was insufficient. With the continuous advancement of the interconnection and intercommunication between industrial control system networks, and the increasing number of industrial control systems and industrial equipment connected to the Internet, the possibility of attacks on industrial control systems through the Internet is increasing, and new The number of SCADA, DCS, and PLC vulnerabilities discovered is also increasing, all of which bring huge security risks to the Industrial Internet. Since 2011, various vulnerabilities in industrial control systems have been increasing at a high speed every year. These vulnerabilities will become a main way to attack industrial control networks. Through these vulnerabilities, attacks can be completed to obtain system permissions, modify engineering data and control processes, Illegal shutdown of on-site equipment and other operations has caused major production accidents and economic losses. Industrial control network vulnerabilities Industrial control network equipment is distributed throughout the plant, even in the field. Due to the limitations of the network infrastructure, common transmission methods such as wireless network, satellite, GPRS/CDMA are often needed to realize the connection and data exchange with the dispatch center. Without adequate security protection and encryption measures, these transmission methods are prone to security problems such as network eavesdropping, data hijacking, and third-party attacks. In addition, attackers can also use insecure transmission methods as the entrance to attack the industrial control network to achieve the entire Penetration and control of industrial control networks. Cloud platform security issues In the cloud platform, virtualization technology, as the underlying support technology, not only brings efficiency improvement and cost reduction, but also brings a series of data security problems due to the conflict between physical sharing and logical isolation. In the public cloud environment, the physically isolated network between different institutions is replaced by a virtual network constructed by network virtualization technology. Although this network resource multiplexing mode realizes the efficient use of network resources and the centralized distribution of network traffic, it also brings many security problems. Penetration from external networks There will be many open services on the Industrial Internet. Attackers can discover open services through scanning, and use the vulnerabilities and defects in the open services to log in to the network server to obtain key corporate information. Tongjin can also use the office network as a springboard to gradually penetrate Control the network. Through a series of infiltrations and attacks on the office network and control network, the company's important production materials and key formulas are finally obtained. The serious thing is to randomly change the switch status of the control instrument and maliciously modify its control volume, causing major production accidents. Account password cracking Because companies have open application systems (such as mail systems), they need to be authenticated when logging in to open application systems. Attacks are all through weak password scanning, Sniffer password sniffing, brute force cracking, trusted person sniffing, or social work comparison synthesis Passwords and other means to obtain the user's password, so as to directly obtain system or application permissions. Once the user authority is obtained, the relevant information can be retrieved and the relevant control facilities can be maliciously changed. Attack with mobile media When the mobile medium with malicious programs is connected to the engineer station or the operator station, the mobile medium virus will use the self-running function of the mobile medium to automatically initiate a malicious attack on the control device or a malicious command. On the one hand, the network virus automatically spreads and infects at all network levels of the enterprise, and the performance of the business system and control system is reduced, which affects the enterprise's monitoring, overall planning, and decision-making capabilities. On the other hand, it will maliciously change the actual control amount of a specific control system or device, causing an accident. Threat of PLC program virus Through the control of the engineering station and the programming server, the related programs are infected (replaced). When the PLC program is issued, the malicious program is also issued to the PLC control equipment. On the one hand, the malicious program tampers with the actual control flow of the PLC, and on the other hand sends the calculated false data to the output of the PLC to prevent alarms. In this way, the pressure, temperature, and liquid level of the field equipment are out of control, but the monitoring system cannot detect it in time, causing a major safety accident. Utilize the pitfalls of industrial communication protocols Traditional industrial protocols such as Modbus, DNP3, and OPC lack security mechanisms such as identity authentication, authorization, and encryption. They use man-in-the-middle attacks to capture and tamper with data, issue malicious instructions to equipment, affect production scheduling, and cause production out of control. Use wireless network intrusion The control network is connected to the management area network through the DTU wireless device through the 802.11b protocol. Through the collection of network wireless information, the WEP security protocol vulnerabilities are detected, the communication between the wireless access device and the customer is cracked, and the access password is analyzed. So as to successfully access the control network, control the field equipment, obtain confidential information, change the control status of the control system and equipment, and cause a significant impact. The Industrial Internet realizes the all-round connection of equipment, factories, people, and products. Therefore, the security construction of the Industrial Internet must be planned as a whole from the perspective of a comprehensive security protection system. From the perspective of the overall architecture of the Industrial Internet, corresponding security protection measures should be implemented at all levels, and various security technologies and security such as intrusion detection, boundary protection, protocol analysis, behavior analysis, security auditing, disaster recovery backup, situational awareness, etc. should be implemented. The combination of management realizes the security protection of the Industrial Internet, and forms a closed loop of "monitoring, alarm, disposal, traceability, recovery, and inspection" of the industrial Internet security. Pin Header,Smd Pin Header,Double Row Pin Connector,Environmentally Friendly Pin Headers Shenzhen Jinyicheng Electronci Technology Co.,Ltd. , https://www.jycconnector.com