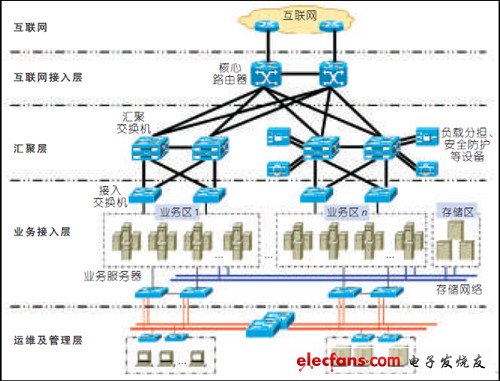
This article introduces the main characteristics of the Internet data center network architecture and multi-layer design principles, analyzes the main security threats faced by the Internet data center, and proposes proposals for its security planning and deployment implementation. 1 Internet data center network multi-layer design principles In essence, the multi-layer design principle of the Internet data center network is to divide the area, divide the layer, and each is responsible for the security defense task. That is, the complex data center internal network and host elements are divided into multiple layers and multiple parts according to certain principles to form Good logical hierarchy and partitioning. The business of data center users can be divided into multiple subsystems. There will be data sharing, business mutual access, data access control and isolation requirements between each other. According to business relevance and process requirements, a modular design is required to achieve low coupling, High cohesion, to ensure the security, reliability, flexibility, scalability, and ease of management of the system and data Own separate core switches, servers, security border devices, etc., level-by-level access control, and adopt different levels of security measures and protection methods. The Internet data center network can be divided into layers and areas from various aspects at the same time: (1) Stratification according to the principle of internal and external partial flow. (2) According to the principle of business module isolation. (3) According to the application of hierarchical access principles to grade. ▲ Figure 1 Data center network layering 1.1 Layering According to the internal and external split principle, the data center network can be divided into 4 layers: Internet access layer, convergence layer, service access layer and operation and maintenance management layer. The most common data center network layering is shown in Figure 1. The Internet access layer is configured with core routers to realize interconnection with the Internet, convert and maintain routing information of the Internet data center's internal and external networks, and connect to the aggregation switches of the aggregation layer to form the network core of the data center. The aggregation layer is configured with aggregation switches to converge the access switches of each service area of ​​the service access layer downward and interconnect with the core router upward. Some traffic management equipment and security equipment are deployed at this layer. Large customers or key services can directly access the aggregation layer switches. The service access layer accesses various server devices and network devices in each service area through access switches. The operation and maintenance management layer is generally independently networked, isolated from the business network, and connected to various devices of the management subsystem through the access and aggregation switches of the operation and maintenance management layer. 1.2 Partition According to different needs in terms of relevance, management, and security protection, the data center network can be divided into different areas: Internet domain, access domain, service domain, management domain, computing domain, etc., and each security domain is isolated by a firewall To ensure appropriate access control strategies. The Internet domain includes management users implementing self-service management and end users accessing applications. The access domain provides a unified interface and excuse for users to access the data center, also known as a demilitarized zone (DMZ). The service domain provides network service functions such as domain name resolution, identity authentication and authorization, and IP address translation. The computing domain provides computing services, and security subdomains can be further divided according to security requirements. The management domain provides security management, operation management, and business management. Relatively speaking, the computing domain and the management domain have the highest security levels, followed by the service domain and the access domain, and the user domain the lowest. Victron Mega Fuse,Victron Fuse Holder,Victron Mega Fuse Holder,Victron Fuse Dongguan Andu Electronic Co., Ltd. , https://www.autoido.com