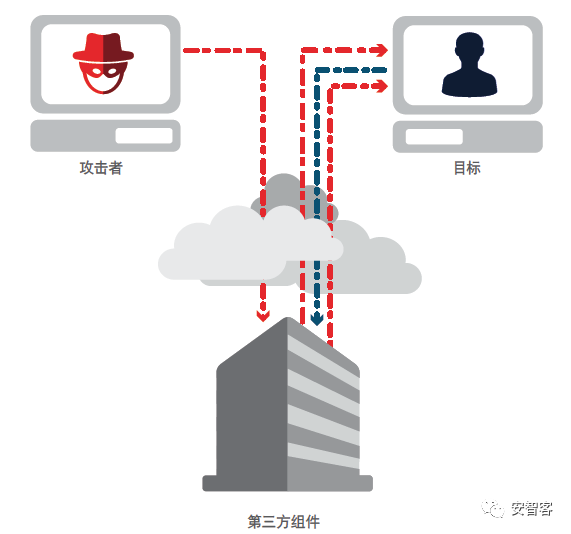
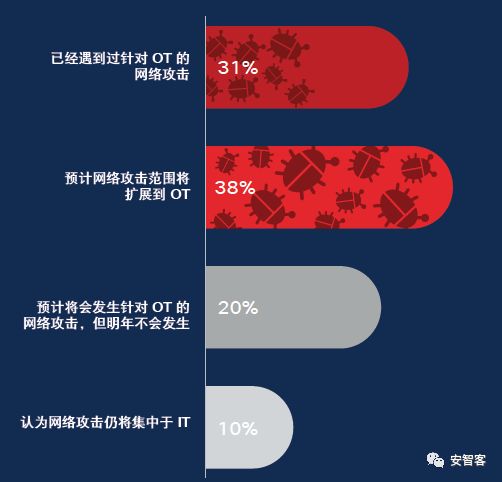
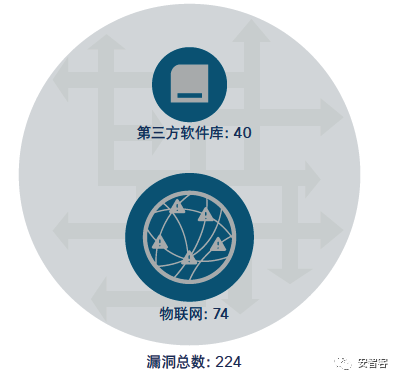
Cisco publishes cybersecurity reports annually and the latest 2018 annual cybersecurity report presents data and analysis from Cisco researchers and their partners based on the behavior of the attackers observed over the past 12 to 18 months. The report revolves around three topics: 1. Attackers have increased the complexity and influence of malware to an unprecedented level. 2. Attackers are getting better at avoiding and turning cloud services and other technologies used for legitimate purposes into weapons. 3. Attackers exploit unguarded security vulnerabilities, many of which originate from the ever-expanding Internet of Things (IoT) and cloud services. The Cisco Security Report devoted a lot of space to IoT security. Cisco believes: The Internet of Things is still evolving, but attackers have begun to use the security vulnerabilities of IoT devices to gain system access, including industrial control systems that support critical infrastructure. In terms of scale and power, the Internet of Things botnet is also growing and it can gradually launch powerful attacks and cause serious damage to the Internet. Attackers have increased their use of application-level vulnerabilities. This trend indicates that this has become their target. However, many security experts do not realize or ignore the threat posed by the Internet of Things botnet. Organizations continue to add IoT devices to their IT environments, with little or no thought of security issues. What's worse, they don't even spend time calculating how many IoT devices connect to their networks. This makes it easy for attackers to control the Internet of Things. The 2017 Cisco Cyber ​​Security Report provided analysis of the three Internet of Things botnets Mirai, Brickerbot, and Hajimeand. The latest report in 2018 revisited the IoT botnet theme, highlighting the seriousness of the threat. Because IoT devices are powered by Linux and Unix systems, they tend to be targets of executable and linkable format (ELF) binaries. Operators' control of IoT devices is not as good as that of PCs, which means that it is easy for attackers to build up a "big army" in a short time. IoT attacks have the following characteristics: 1. At the same time as network layer attacks are reduced, application layer attacks are increasing. 2. The complexity, frequency, and duration of "burst attacks" increase. 3, Reflection amplification attacks use potentially legitimate third-party components to send attack traffic to the target, hiding the identity of the attacker. The attacker sends the packet to the reflector server and sets the source IP address to the target user IP. This indirectly floods the target with response packets, exhausting the target's available resources. 4. For IoT devices, bug fixes are slow or not at all. Security personnel studied the repair trend of IoT devices. The devices in the sample include IP-enabled HVAC systems, door locks, fire alarm panels, and card readers. A total of 7,328 devices were tested, but only 1,206 were repaired. Cisco believes that more and more operational technologies and IoT attacks are coming soon! Although current attacks on industrial control systems and IoT devices are still rare, Cisco research on the Security Capability Benchmark Study in 2018 fully recognizes such attacks. (OT: refers to operational technologies such as industrial control systems and IoT devices) From October 1, 2016 to September 30, 2017, Cisco threat researchers discovered 224 new vulnerabilities in non-Cisco products, of which 40 vulnerabilities were related to third-party software libraries included in these products. Networked devices. An Zhike Note: This is consistent with the description of the Android Security Annual Report. Due to problems caused by third-party libraries, Android O has modified the Android architecture. Display Port And Mini Display Port Display Port And Mini Display Port Display Port ,Mini Display Port ShenZhen Antenk Electronics Co,Ltd , https://www.antenksocket.com